This is the multi-page printable view of this section. Click here to print.
Query connectivity plugins
1 - ai_embed_text plugin (Preview)
The ai_embed_text plugin allows embedding of text using language models, enabling various AI-related scenarios such as Retrieval Augmented Generation (RAG) applications and semantic search. The plugin supports Azure OpenAI Service embedding models accessed using managed identity.
Prerequisites
- An Azure OpenAI Service configured with managed identity
- Managed identity and callout policies configured to allow communication with Azure OpenAI services
Syntax
evaluate ai_embed_text (text, connectionString [, options [, IncludeErrorMessages]])
Parameters
| Name | Type | Required | Description |
|---|---|---|---|
| text | string | ✔️ | The text to embed. The value can be a column reference or a constant scalar. |
| connectionString | string | ✔️ | The connection string for the language model in the format <ModelDeploymentUri>;<AuthenticationMethod>; replace <ModelDeploymentUri> and <AuthenticationMethod> with the AI model deployment URI and the authentication method respectively. |
| options | dynamic | The options that control calls to the embedding model endpoint. See Options. | |
| IncludeErrorMessages | bool | Indicates whether to output errors in a new column in the output table. Default value: false. |
Options
The following table describes the options that control the way the requests are made to the embedding model endpoint.
| Name | Type | Description |
|---|---|---|
RecordsPerRequest | int | Specifies the number of records to process per request. Default value: 1. |
CharsPerRequest | int | Specifies the maximum number of characters to process per request. Default value: 0 (unlimited). Azure OpenAI counts tokens, with each token approximately translating to four characters. |
RetriesOnThrottling | int | Specifies the number of retry attempts when throttling occurs. Default value: 0. |
GlobalTimeout | timespan | Specifies the maximum time to wait for a response from the embedding model. Default value: null |
ModelParameters | dynamic | Parameters specific to the embedding model, such as embedding dimensions or user identifiers for monitoring purposes. Default value: null. |
Configure managed identity and callout policies
To use the ai_embed_text plugin, you must configure the following policies:
- managed identity: Allow the system-assigned managed identity to authenticate to Azure OpenAI services.
- callout: Authorize the AI model endpoint domain.
To configure these policies, use the commands in the following steps:
Configure the managed identity:
.alter-merge cluster policy managed_identity ``` [ { "ObjectId": "system", "AllowedUsages": "AzureAI" } ] ```Configure the callout policy:
.alter-merge cluster policy callout ``` [ { "CalloutType": "azure_openai", "CalloutUriRegex": "https://[A-Za-z0-9\\-]{3,63}\\.openai\\.azure\\.com/.*", "CanCall": true } ] ```
Returns
Returns the following new embedding columns:
- A column with the _embedding suffix that contains the embedding values
- If configured to return errors, a column with the _embedding_error suffix, which contains error strings or is left empty if the operation is successful.
Depending on the input type, the plugin returns different results:
- Column reference: Returns one or more records with additional columns are prefixed by the reference column name. For example, if the input column is named TextData, the output columns are named TextData_embedding and, if configured to return errors, TextData_embedding_error.
- Constant scalar: Returns a single record with additional columns that are not prefixed. The column names are _embedding and, if configured to return errors, _embedding_error.
Examples
The following example embeds the text Embed this text using AI using the Azure OpenAI Embedding model.
let expression = 'Embed this text using AI';
let connectionString = 'https://myaccount.openai.azure.com/openai/deployments/text-embedding-3-small/embeddings?api-version=2024-06-01;managed_identity=system';
evaluate ai_embed_text(expression, connectionString)
The following example embeds multiple texts using the Azure OpenAI Embedding model.
let connectionString = 'https://myaccount.openai.azure.com/openai/deployments/text-embedding-3-small/embeddings?api-version=2024-06-01;managed_identity=system';
let options = dynamic({
"RecordsPerRequest": 10,
"CharsPerRequest": 10000,
"RetriesOnThrottling": 1,
"GlobalTimeout": 2m
});
datatable(TextData: string)
[
"First text to embed",
"Second text to embed",
"Third text to embed"
]
| evaluate ai_embed_text(TextData, connectionString, options , true)
Best practices
Azure OpenAI embedding models are subject to heavy throttling, and frequent calls to this plugin can quickly reach throttling limits.
To efficiently use the ai_embed_text plugin while minimizing throttling and costs, follow these best practices:
- Control request size: Adjust the number of records (
RecordsPerRequest) and characters per request (CharsPerRequest). - Control query timeout: Set
GlobalTimeoutto a value lower than the query timeout to ensure progress isn’t lost on successful calls up to that point. - Handle rate limits more gracefully: Set retries on throttling (
RetriesOnThrottling).
Related content
2 - azure_digital_twins_query_request plugin
The azure_digital_twins_query_request plugin runs an Azure Digital Twins query as part of a Kusto Query Language (KQL) query. The plugin is invoked with the evaluate operator.
Using the plugin, you can query across data in both Azure Digital Twins and any data source accessible through KQL. For example, you can perform time series analytics.
For more information about the plugin, see Azure Digital Twins query plugin.
Syntax
evaluate azure_digital_twins_query_request ( AdtInstanceEndpoint , AdtQuery )
Parameters
| Name | Type | Required | Description |
|---|---|---|---|
| AdtInstanceEndpoint | string | ✔️ | The Azure Digital Twins instance endpoint to be queried. |
| AdtQuery | string | ✔️ | The query to run against the Azure Digital Twins endpoint. This query is written in a custom SQL-like query language for Azure Digital Twins, called the Azure Digital Twins query language. For more information, see Query language for Azure Digital Twins. |
Authentication and authorization
The azure_digital_twins_query_request plugin uses the Microsoft Entra account of the user running the query to authenticate. To run a query, a user must at least be granted the Azure Digital Twins Data Reader role. Information on how to assign this role can be found in Security for Azure Digital Twins solutions.
Examples
The following examples show how you can run various Azure Digital Twins queries, including queries that use additional Kusto expressions.
Retrieval of all twins within an Azure Digital Twins instance
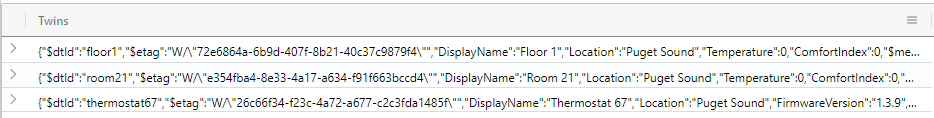
The following example returns all digital twins within an Azure Digital Twins instance.
evaluate azure_digital_twins_query_request(
'https://contoso.api.wcus.digitaltwins.azure.net',
'SELECT T AS Twins FROM DIGITALTWINS T')
Projection of twin properties as columns along with additional Kusto expressions
The following example returns the result from the plugin as separate columns, and then performs additional operations using Kusto expressions.
evaluate azure_digital_twins_query_request(
'https://contoso.api.wcus.digitaltwins.azure.net',
'SELECT T.Temperature, T.Humidity FROM DIGITALTWINS T WHERE IS_PRIMITIVE(T.Temperature) AND IS_PRIMITIVE(T.Humidity)')
| where Temperature > 20
| project TemperatureInC = Temperature, Humidity
Output
| TemperatureInC | Humidity |
|---|---|
| 21 | 48 |
| 49 | 34 |
| 80 | 32 |
Perform time series analytics
You can use the data history integration feature of Azure Digital Twins to historize digital twin property updates. To learn how to view the historized twin updates, see View the historized twin updates
3 - cosmosdb_sql_request plugin
The cosmosdb_sql_request plugin sends a SQL query to an Azure Cosmos DB SQL network endpoint and returns the results of the query. This plugin is primarily designed for querying small datasets, for example, enriching data with reference data stored in Azure Cosmos DB. The plugin is invoked with the evaluate operator.
Syntax
evaluate cosmosdb_sql_request ( ConnectionString , SqlQuery [, SqlParameters [, Options]] ) [: OutputSchema]
Parameters
| Name | Type | Required | Description |
|---|---|---|---|
| ConnectionString | string | ✔️ | The connection string that points to the Azure Cosmos DB collection to query. It must include AccountEndpoint, Database, and Collection. It might include AccountKey if a master key is used for authentication. For more information, see Authentication and authorization.Example: 'AccountEndpoint=https://cosmosdbacc.documents.azure.com/;Database=<MyDatabase>;Collection=<MyCollection>;AccountKey='h'<AccountKey>' |
| SqlQuery | string | ✔️ | The query to execute. |
| SqlParameters | dynamic | The property bag object to pass as parameters along with the query. Parameter names must begin with @. | |
| OutputSchema | The names and types of the expected columns of the cosmosdb_sql_request plugin output. Use the following syntax: ( ColumnName : ColumnType [, …] ). Specifying this parameter enables multiple query optimizations. | ||
| Options | dynamic | A property bag object of advanced settings. If an AccountKey isn’t provided in the ConnectionString, then the armResourceId field of this parameter is required. For more information, see Supported options. |
Supported options
The following table describes the supported fields of the Options parameter.
| Name | Type | Description |
|---|---|---|
armResourceId | string | The Azure Resource Manager resource ID of the Cosmos DB database. If an account key isn’t provided in the connection string argument, this field is required. In such a case, the armResourceId is used to authenticate to Cosmos DB.Example: armResourceId='/subscriptions/<SubscriptionId>/resourceGroups/<ResourceGroup>/providers/Microsoft.DocumentDb/databaseAccounts/<DatabaseAccount>' |
token | string | A Microsoft Entra access token of a principal with access to the Cosmos DB database. This token is used along with the armResourceId to authenticate with the Azure Resource Manager. If unspecified, the token of the principal that made the query is used.If armResourceId isn’t specified, the token is used directly to access the Cosmos DB database. For more information about the token authentication method, see Authentication and authorization. |
preferredLocations | string | The region from which to query the data.Example: ['East US'] |
Authentication and authorization
To authorize to an Azure Cosmos DB SQL network endpoint, you need to specify the authorization information. The following table provides the supported authentication methods and the description for how to use that method.
| Authentication method | Description |
|---|---|
| Managed identity (Recommended) | Append Authentication="Active Directory Managed Identity";User Id={object_id}; to the connection string. The request is made on behalf of a managed identity which must have the appropriate permissions to the database.To enable managed identity authentication, you must add the managed identity to your cluster and alter the managed identity policy. For more information, see Managed Identity policy. |
| Azure Resource Manager resource ID | This authentication method requires specifying the armResourceId and optionally the token in the options. The armResourceId identifies the Cosmos DB database account, and the token must be a valid Microsoft Entra bearer token for a principal with access permissions to the Cosmos DB database. If no token is provided, the Microsoft Entra token of the requesting principal will be used for authentication. |
| Account key | You can add the account key directly to the ConnectionString argument. However, this approach is less secure as it involves including the secret in the query text, and is less resilient to future changes in the account key. To enhance security, hide the secret as an obfuscated string literal. |
| Token | You can add a token value in the plugin options. The token must belong to a principal with relevant permissions. To enhance security, hide the token as an obfuscated string literal. |
Set callout policy
The plugin makes callouts to the Azure Cosmos DB instance. Make sure that the cluster’s callout policy enables calls of type cosmosdb to the target CosmosDbUri.
The following example shows how to define the callout policy for Azure Cosmos DB. It’s recommended to restrict it to specific endpoints (my_endpoint1, my_endpoint2).
[
{
"CalloutType": "CosmosDB",
"CalloutUriRegex": "my_endpoint1\\.documents\\.azure\\.com",
"CanCall": true
},
{
"CalloutType": "CosmosDB",
"CalloutUriRegex": "my_endpoint2\\.documents\\.azure\\.com",
"CanCall": true
}
]
The following example shows an alter callout policy command for cosmosdb CalloutType
.alter cluster policy callout @'[{"CalloutType": "cosmosdb", "CalloutUriRegex": "\\.documents\\.azure\\.com", "CanCall": true}]'
Examples
The following examples use placeholder text, in brackets.
Query Azure Cosmos DB with a query-defined output schema
The following example uses the cosmosdb_sql_request plugin to send a SQL query while selecting only specific columns. This query uses explicit schema definitions that allow various optimizations before the actual query is run against Cosmos DB.
evaluate cosmosdb_sql_request(
'AccountEndpoint=https://cosmosdbacc.documents.azure.com/;Database=<MyDatabase>;Collection=<MyCollection>;AccountKey='h'<AccountKey>',
'SELECT c.Id, c.Name from c') : (Id:long, Name:string)
Query Azure Cosmos DB
The following example uses the cosmosdb_sql_request plugin to send a SQL query to fetch data from Azure Cosmos DB using its Azure Cosmos DB for NoSQL.
evaluate cosmosdb_sql_request(
'AccountEndpoint=https://cosmosdbacc.documents.azure.com/;Database=<MyDatabase>;Collection=<MyCollection>;AccountKey='h'<AccountKey>',
'SELECT * from c') // OutputSchema is unknown, so it is not specified. This may harm the performance of the query.
Query Azure Cosmos DB with parameters
The following example uses SQL query parameters and queries the data from an alternate region. For more information, see preferredLocations.
evaluate cosmosdb_sql_request(
'AccountEndpoint=https://cosmosdbacc.documents.azure.com/;Database=<MyDatabase>;Collection=<MyCollection>;AccountKey='h'<AccountKey>',
"SELECT c.id, c.lastName, @param0 as Column0 FROM c WHERE c.dob >= '1970-01-01T00:00:00Z'",
dynamic({'@param0': datetime(2019-04-16 16:47:26.7423305)}),
dynamic({'preferredLocations': ['East US']})) : (Id:long, Name:string, Column0: datetime)
| where lastName == 'Smith'
Query Azure Cosmos DB and join data with a database table
The following example joins partner data from an Azure Cosmos DB with partner data in a database using the Partner field. It results in a list of partners with their phone numbers, website, and contact email address sorted by partner name.
evaluate cosmosdb_sql_request(
'AccountEndpoint=https://cosmosdbacc.documents.azure.com/;Database=<MyDatabase>;Collection=<MyCollection>;AccountKey='h'<AccountKey>',
"SELECT c.id, c.Partner, c. phoneNumber FROM c') : (Id:long, Partner:string, phoneNumber:string)
| join kind=innerunique Partner on Partner
| project id, Partner, phoneNumber, website, Contact
| sort by Partner
Query Azure Cosmos DB using token authentication
The following example joins partner data from an Azure Cosmos DB with partner data in a database using the Partner field. It results in a list of partners with their phone numbers, website, and contact email address sorted by partner name.
evaluate cosmosdb_sql_request(
'AccountEndpoint=https://cosmosdbacc.documents.azure.com/;Database=<MyDatabase>;Collection=<MyCollection>;',
"SELECT c.Id, c.Name, c.City FROM c",
dynamic(null),
dynamic({'token': h'abc123...'})
) : (Id:long, Name:string, City:string)
Query Azure Cosmos DB using Azure Resource Manager resource ID for authentication
The following example uses the Azure Resource Manager resource ID for authentication and the Microsoft Entra token of the requesting principal, since a token isn’t specified. It sends a SQL query while selecting only specific columns and specifies explicit schema definitions.
evaluate cosmosdb_sql_request(
'AccountEndpoint=https://cosmosdbacc.documents.azure.com/;Database=<MyDatabase>;Collection=<MyCollection>;',
"SELECT c.Id, c.Name, c.City FROM c",
dynamic({'armResourceId': '/subscriptions/<SubscriptionId>/resourceGroups/<ResourceGroup>/providers/Microsoft.DocumentDb/databaseAccounts/<DatabaseAccount>'})
) : (Id:long, Name:string, City:string)
4 - http_request plugin
services: data-explorer
http_request plugin
The http_request plugin sends an HTTP GET request and converts the response into a table.
Prerequisites
- Run
.enable plugin http_requestto enable the plugin - Set the URI to access as an allowed destination for
webapiin the Callout policy
Syntax
evaluate http_request ( Uri [, RequestHeaders [, Options]] )
Parameters
| Name | Type | Required | Description |
|---|---|---|---|
| Uri | string | ✔️ | The destination URI for the HTTP or HTTPS request. |
| RequestHeaders | dynamic | A property bag containing HTTP headers to send with the request. | |
| Options | dynamic | A property bag containing additional properties of the request. |
Authentication and authorization
To authenticate, use the HTTP standard Authorization header or any custom header supported by the web service.
Returns
The plugin returns a table that has a single record with the following dynamic columns:
- ResponseHeaders: A property bag with the response header.
- ResponseBody: The response body parsed as a value of type
dynamic.
If the HTTP response indicates (via the Content-Type response header) that the media type is application/json,
the response body is automatically parsed as-if it’s a JSON object. Otherwise, it’s returned as-is.
Headers
The RequestHeaders argument can be used to add custom headers to the outgoing HTTP request. In addition to the standard HTTP request headers and the user-provided custom headers, the plugin also adds the following custom headers:
| Name | Description |
|---|---|
x-ms-client-request-id | A correlation ID that identifies the request. Multiple invocations of the plugin in the same query will all have the same ID. |
x-ms-readonly | A flag indicating that the processor of this request shouldn’t make any persistent changes. |
Example
The following example retrieves Azure retails prices for Azure Purview in west Europe:
let Uri = "https://prices.azure.com/api/retail/prices?$filter=serviceName eq 'Azure Purview' and location eq 'EU West'";
evaluate http_request(Uri)
| project ResponseBody.Items
| mv-expand ResponseBody_Items
| evaluate bag_unpack(ResponseBody_Items)
Output
| armRegionName | armSkuName | currencyCode | effectiveStartDate | isPrimaryMeterRegion | location | meterId | meterName | productId | productName | retailPrice | serviceFamily | serviceId | serviceName | skuId | skuName | tierMinimumUnits | type | unitOfMeasure | unitPrice |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| westeurope | Data Insights | USD | 2022-06-01T00:00:00Z | false | EU West | 8ce915f7-20db-564d-8cc3-5702a7c952ab | Data Insights Report Consumption | DZH318Z08M22 | Azure Purview Data Map | 0.21 | Analytics | DZH318Q66D0F | Azure Purview | DZH318Z08M22/006C | Catalog Insights | 0 | Consumption | 1 API Calls | 0.21 |
| westeurope | Data Map Enrichment - Data Insights Generation | USD | 2022-06-01T00:00:00Z | false | EU West | 7ce2db1d-59a0-5193-8a57-0431a10622b6 | Data Map Enrichment - Data Insights Generation vCore | DZH318Z08M22 | Azure Purview Data Map | 0.82 | Analytics | DZH318Q66D0F | Azure Purview | DZH318Z08M22/005C | Data Map Enrichment - Insight Generation | 0 | Consumption | 1 Hour | 0.82 |
| westeurope | USD | 2021-09-28T00:00:00Z | false | EU West | 053e2dcb-82c0-5e50-86cd-1f1c8d803705 | Power BI vCore | DZH318Z08M23 | Azure Purview Scanning Ingestion and Classification | 0 | Analytics | DZH318Q66D0F | Azure Purview | DZH318Z08M23/0005 | Power BI | 0 | Consumption | 1 Hour | 0 | |
| westeurope | USD | 2021-09-28T00:00:00Z | false | EU West | a7f57f26-5f31-51e5-a5ed-ffc2b0da37b9 | Resource Set vCore | DZH318Z08M22 | Azure Purview Data Map | 0.21 | Analytics | DZH318Q66D0F | Azure Purview | DZH318Z08M22/000X | Resource Set | 0 | Consumption | 1 Hour | 0.21 | |
| westeurope | USD | 2021-09-28T00:00:00Z | false | EU West | 5d157295-441c-5ea7-ba7c-5083026dc456 | SQL Server vCore | DZH318Z08M23 | Azure Purview Scanning Ingestion and Classification | 0 | Analytics | DZH318Q66D0F | Azure Purview | DZH318Z08M23/000F | SQL Server | 0 | Consumption | 1 Hour | 0 | |
| westeurope | USD | 2021-09-28T00:00:00Z | false | EU West | 0745df0d-ce4f-52db-ac31-ac574d4dcfe5 | Standard Capacity Unit | DZH318Z08M22 | Azure Purview Data Map | 0.411 | Analytics | DZH318Q66D0F | Azure Purview | DZH318Z08M22/0002 | Standard | 0 | Consumption | 1 Hour | 0.411 | |
| westeurope | USD | 2021-09-28T00:00:00Z | false | EU West | 811e3118-5380-5ee8-a5d9-01d48d0a0627 | Standard vCore | DZH318Z08M23 | Azure Purview Scanning Ingestion and Classification | 0.63 | Analytics | DZH318Q66D0F | Azure Purview | DZH318Z08M23/0009 | Standard | 0 | Consumption | 1 Hour | 0.63 |
5 - http_request_post plugin
services: data-explorer
http_request_post plugin
The http_request_post plugin sends an HTTP POST request and converts the response into a table.
Prerequisites
- Run
.enable plugin http_request_postto enable the plugin - Set the URI to access as an allowed destination for
webapiin the Callout policy
Syntax
evaluate http_request_post ( Uri [, RequestHeaders [, Options [, Content]]] )
Parameters
| Name | Type | Required | Description |
|---|---|---|---|
| Uri | string | ✔️ | The destination URI for the HTTP or HTTPS request. |
| RequestHeaders | dynamic | A property bag containing HTTP headers to send with the request. | |
| Options | dynamic | A property bag containing additional properties of the request. | |
| Content | string | The body content to send with the request. The content is encoded in UTF-8 and the media type for the Content-Type attribute is application/json. |
Authentication and authorization
To authenticate, use the HTTP standard Authorization header or any custom header supported by the web service.
Returns
The plugin returns a table that has a single record with the following dynamic columns:
- ResponseHeaders: A property bag with the response header.
- ResponseBody: The response body parsed as a value of type
dynamic.
If the HTTP response indicates (via the Content-Type response header) that the media type is application/json,
the response body is automatically parsed as-if it’s a JSON object. Otherwise, it’s returned as-is.
Headers
The RequestHeaders argument can be used to add custom headers to the outgoing HTTP request. In addition to the standard HTTP request headers and the user-provided custom headers, the plugin also adds the following custom headers:
| Name | Description |
|---|---|
x-ms-client-request-id | A correlation ID that identifies the request. Multiple invocations of the plugin in the same query will all have the same ID. |
x-ms-readonly | A flag indicating that the processor of this request shouldn’t make any persistent changes. |
Example
The following example is for a hypothetical HTTPS web service that accepts additional request headers and must be authenticated to using Microsoft Entra ID:
let uri='https://example.com/node/js/on/eniac';
let headers=dynamic({'x-ms-correlation-vector':'abc.0.1.0', 'authorization':'bearer ...Azure-AD-bearer-token-for-target-endpoint...'});
evaluate http_request_post(uri, headers)
6 - mysql_request plugin
The mysql_request plugin sends a SQL query to an Azure MySQL Server network endpoint and returns the first rowset in the results. The query may return more than one rowset, but only the first rowset is made available for the rest of the Kusto query.
The plugin is invoked with the evaluate operator.
Syntax
evaluate mysql_request ( ConnectionString , SqlQuery [, SqlParameters] ) [: OutputSchema]
Parameters
| Name | Type | Required | Description |
|---|---|---|---|
| ConnectionString | string | ✔️ | The connection string that points at the MySQL Server network endpoint. See authentication and how to specify the network endpoint. |
| SqlQuery | string | ✔️ | The query that is to be executed against the SQL endpoint. Must return one or more row sets. Only the first set is made available for the rest of the query. |
| SqlParameters | dynamic | A property bag object that holds key-value pairs to pass as parameters along with the query. | |
| OutputSchema | The names and types for the expected columns of the mysql_request plugin output.Syntax: ( ColumnName : ColumnType [, …] ) |
Authentication and authorization
To authorize to a MySQL Server network endpoint, you need to specify the authorization information in the connection string. The supported authorization method is via username and password.
Set callout policy
The plugin makes callouts to the MySql database. Make sure that the cluster’s callout policy enables calls of type mysql to the target MySqlDbUri.
The following example shows how to define the callout policy for MySQL databases. We recommend restricting the callout policy to specific endpoints (my_endpoint1, my_endpoint2).
[
{
"CalloutType": "mysql",
"CalloutUriRegex": "my_endpoint1\\.mysql\\.database\\.azure\\.com",
"CanCall": true
},
{
"CalloutType": "mysql",
"CalloutUriRegex": "my_endpoint2\\.mysql\\.database\\.azure\\.com",
"CanCall": true
}
]
The following example shows an .alter callout policy command for mysql CalloutType:
.alter cluster policy callout @'[{"CalloutType": "mysql", "CalloutUriRegex": "\\.mysql\\.database\\.azure\\.com", "CanCall": true}]'
Username and password authentication
The mysql_request plugin only supports username and password authentication to the MySQL server endpoint and doesn’t integrate with Microsoft Entra authentication.
The username and password are provided as part of the connections string using the following parameters:
User ID=...; Password=...;
Encryption and server validation
For security, SslMode is unconditionally set to Required when connecting to a MySQL server network endpoint. As a result, the server must be configured with a valid SSL/TLS server certificate.
Specify the network endpoint
Specify the MySQL network endpoint as part of the connection string.
Syntax:
Server = FQDN [Port = Port]
Where:
- FQDN is the fully qualified domain name of the endpoint.
- Port is the TCP port of the endpoint. By default,
3306is assumed.
Examples
SQL query to Azure MySQL DB
The following example sends a SQL query to an Azure MySQL database. It retrieves all records from [dbo].[Table], and then processes the results.
evaluate mysql_request(
'Server=contoso.mysql.database.azure.com; Port = 3306;'
'Database=Fabrikam;'
h'UID=USERNAME;'
h'Pwd=PASSWORD;',
'select * from `dbo`.`Table`') : (Id: int, Name: string)
| where Id > 0
| project Name
SQL query to an Azure MySQL database with modifications
The following example sends a SQL query to an Azure MySQL database
retrieving all records from [dbo].[Table], while appending another datetime column,
and then processes the results on the Kusto side.
It specifies a SQL parameter (@param0) to be used in the SQL query.
evaluate mysql_request(
'Server=contoso.mysql.database.azure.com; Port = 3306;'
'Database=Fabrikam;'
h'UID=USERNAME;'
h'Pwd=PASSWORD;',
'select *, @param0 as dt from `dbo`.`Table`',
dynamic({'param0': datetime(2020-01-01 16:47:26.7423305)})) : (Id:long, Name:string, dt: datetime)
| where Id > 0
| project Name
SQL query to an Azure MySQL database without a query-defined output schema
The following example sends a SQL query to an Azure MySQL database without an output schema. This is not recommended unless the schema is unknown, as it may impact the performance of the query.
evaluate mysql_request(
'Server=contoso.mysql.database.azure.com; Port = 3306;'
'Database=Fabrikam;'
h'UID=USERNAME;'
h'Pwd=PASSWORD;',
'select * from `dbo`.`Table`')
| where Id > 0
| project Name
7 - postgresql_request plugin
The postgresql_request plugin sends a SQL query to an Azure PostgreSQL Server network endpoint and returns the first rowset in the results. The query may return more than one rowset, but only the first rowset is made available for the rest of the Kusto query.
The plugin is invoked with the evaluate operator.
Syntax
evaluate postgresql_request ( ConnectionString , SqlQuery [, SqlParameters] ) [: OutputSchema]
Parameters
| Name | Type | Required | Description |
|---|---|---|---|
| ConnectionString | string | ✔️ | The connection string that points at the PostgreSQL Server network endpoint. See authentication and how to specify the network endpoint. |
| SqlQuery | string | ✔️ | The query that is to be executed against the SQL endpoint. Must return one or more row sets. Only the first set is made available for the rest of the query. |
| SqlParameters | dynamic | A property bag object that holds key-value pairs to pass as parameters along with the query. | |
| OutputSchema | The names and types for the expected columns of the postgresql_request plugin output.Syntax: ( ColumnName : ColumnType [, …] ) |
Authentication and authorization
To authorize a PostgreSQL Server network endpoint, you must specify the authorization information in the connection string. The supported authorization method is via username and password.
Set callout policy
The plugin makes callouts to the PostgreSQL database. Make sure that the cluster’s callout policy enables calls of type postgresql to the target PostgreSqlDbUri.
The following example shows how to define the callout policy for PostgreSQL databases. We recommend restricting the callout policy to specific endpoints (my_endpoint1, my_endpoint2).
[
{
"CalloutType": "postgresql",
"CalloutUriRegex": "my_endpoint1\\.postgres\\.database\\.azure\\.com",
"CanCall": true
},
{
"CalloutType": "postgresql",
"CalloutUriRegex": "my_endpoint2\\.postgres\\.database\\.azure\\.com",
"CanCall": true
}
]
The following example shows a .alter callout policy command for postgresql CalloutType:
.alter cluster policy callout @'[{"CalloutType": "postgresql", "CalloutUriRegex": "\\.postgresql\\.database\\.azure\\.com", "CanCall": true}]'
Username and password authentication
The postgresql_request plugin only supports username and password authentication to the PostgreSQL server endpoint and doesn’t integrate with Microsoft Entra authentication.
The username and password are provided as part of the connections string using the following parameters:
User ID=...; Password=...;
Encryption and server validation
For security, SslMode is unconditionally set to Required when connecting to a PostgreSQL server network endpoint. As a result, the server must be configured with a valid SSL/TLS server certificate.
Specify the network endpoint
Specify the PostgreSQL network endpoint as part of the connection string.
Syntax:
Host = FQDN [Port = Port]
Where:
- FQDN is the fully qualified domain name of the endpoint.
- Port is the TCP port of the endpoint.
Examples
SQL query to Azure PostgreSQL DB
The following example sends a SQL query to an Azure PostgreSQL database. It retrieves all records from public."Table", and then processes the results.
evaluate postgresql_request(
'Host=contoso.postgres.database.azure.com; Port = 5432;'
'Database=Fabrikam;'
h'User Id=USERNAME;'
h'Password=PASSWORD;',
'select * from public."Table"') : (Id: int, Name: string)
| where Id > 0
| project Name
SQL query to an Azure PostgreSQL database with modifications
The following example sends a SQL query to an Azure PostgreSQL database
retrieving all records from public."Table", while appending another datetime column,
and then processes the results.
It specifies a SQL parameter (@param0) to be used in the SQL query.
evaluate postgresql_request(
'Server=contoso.postgres.database.azure.com; Port = 5432;'
'Database=Fabrikam;'
h'User Id=USERNAME;'
h'Password=PASSWORD;',
'select *, @param0 as dt from public."Table"',
dynamic({'param0': datetime(2020-01-01 16:47:26.7423305)})) : (Id: int, Name: string, dt: datetime)
| where Id > 0
| project Name
SQL query to an Azure PostgreSQL database without a query-defined output schema
The following example sends a SQL query to an Azure PostgreSQL database without an output schema. This is not recommended unless the schema is unknown, as it may impact the performance of the query
evaluate postgresql_request(
'Host=contoso.postgres.database.azure.com; Port = 5432;'
'Database=Fabrikam;'
h'User Id=USERNAME;'
h'Password=PASSWORD;',
'select * from public."Table"')
| where Id > 0
| project Name
8 - sql_request plugin
The sql_request plugin sends a SQL query to an Azure SQL Server network endpoint and returns the results.
If more than one rowset is returned by SQL, only the first one is used.
The plugin is invoked with the evaluate operator.
Syntax
evaluate sql_request ( ConnectionString , SqlQuery [, SqlParameters [, Options]] ) [: OutputSchema]
Parameters
| Name | Type | Required | Description |
|---|---|---|---|
| ConnectionString | string | ✔️ | The connection string that points at the SQL Server network endpoint. See valid methods of authentication and how to specify the network endpoint. |
| SqlQuery | string | ✔️ | The query that is to be executed against the SQL endpoint. The query must return one or more row sets, but only the first one is made available for the rest of the Kusto query. |
| SqlParameters | dynamic | A property bag of key-value pairs to pass as parameters along with the query. | |
| Options | dynamic | A property bag of key-value pairs to pass more advanced settings along with the query. Currently, only token can be set, to pass a caller-provided Microsoft Entra access token that is forwarded to the SQL endpoint for authentication. | |
| OutputSchema | string | The names and types for the expected columns of the sql_request plugin output. Use the following syntax: ( ColumnName : ColumnType [, …] ). |
Authentication and authorization
The sql_request plugin supports the following three methods of authentication to the SQL Server endpoint.
|Authentication method|Syntax|How|Description|
|–|–|–|
|Microsoft Entra integrated|Authentication="Active Directory Integrated"|Add to the ConnectionString parameter.| The user or application authenticates via Microsoft Entra ID to your cluster, and the same token is used to access the SQL Server network endpoint.
The principal must have the appropriate permissions on the SQL resource to perform the requested action. For example, to read from the database the principal needs table SELECT permissions, and to write to an existing table the principal needs UPDATE and INSERT permissions. To write to a new table, CREATE permissions are also required.|
|Managed identity|Authentication="Active Directory Managed Identity";User Id={object_id}|Add to the ConnectionString parameter.| The request is executed on behalf of a managed identity. The managed identity must have the appropriate permissions on the SQL resource to perform the requested action.
To enable managed identity authentication, you must add the managed identity to your cluster and alter the managed identity policy. For more information, see Managed Identity policy. |
|Username and password|User ID=...; Password=...;|Add to the ConnectionString parameter.|When possible, avoid this method as it may be less secure.|
|Microsoft Entra access token|dynamic({'token': h"eyJ0..."})|Add in the Options parameter.|The access token is passed as token property in the Options argument of the plugin.|
Examples
Send a SQL query using Microsoft Entra integrated authentication
The following example sends a SQL query to an Azure SQL DB database. It
retrieves all records from [dbo].[Table], and then processes the results on the
Kusto side. Authentication reuses the calling user’s Microsoft Entra token.
evaluate sql_request(
'Server=tcp:contoso.database.windows.net,1433;'
'Authentication="Active Directory Integrated";'
'Initial Catalog=Fabrikam;',
'select * from [dbo].[Table]') : (Id:long, Name:string)
| where Id > 0
| project Name
Send a SQL query using Username/Password authentication
The following example is identical to the previous one, except that SQL authentication is done by username/password. For confidentiality, we use obfuscated strings here.
evaluate sql_request(
'Server=tcp:contoso.database.windows.net,1433;'
'Initial Catalog=Fabrikam;'
h'User ID=USERNAME;'
h'Password=PASSWORD;',
'select * from [dbo].[Table]') : (Id:long, Name:string)
| where Id > 0
| project Name
Send a SQL query using a Microsoft Entra access token
The following example sends a SQL query to an Azure SQL database
retrieving all records from [dbo].[Table], while appending another datetime column,
and then processes the results on the Kusto side.
It specifies a SQL parameter (@param0) to be used in the SQL query.
evaluate sql_request(
'Server=tcp:contoso.database.windows.net,1433;'
'Authentication="Active Directory Integrated";'
'Initial Catalog=Fabrikam;',
'select *, @param0 as dt from [dbo].[Table]',
dynamic({'param0': datetime(2020-01-01 16:47:26.7423305)})) : (Id:long, Name:string, dt: datetime)
| where Id > 0
| project Name
Send a SQL query without a query-defined output schema
The following example sends a SQL query to an Azure SQL database without an output schema. This is not recommended unless the schema is unknown, as it may impact the performance of the query
evaluate sql_request(
'Server=tcp:contoso.database.windows.net,1433;'
'Initial Catalog=Fabrikam;'
h'User ID=USERNAME;'
h'Password=PASSWORD;',
'select * from [dbo].[Table]')
| where Id > 0
| project Name
Encryption and server validation
The following connection properties are forced when connecting to a SQL Server network endpoint, for security reasons.
Encryptis set totrueunconditionally.TrustServerCertificateis set tofalseunconditionally.
As a result, the SQL Server must be configured with a valid SSL/TLS server certificate.
Specify the network endpoint
Specifying the SQL network endpoint as part of the connection string is mandatory. The appropriate syntax is:
Server = tcp: FQDN [, Port]
Where:
- FQDN is the fully qualified domain name of the endpoint.
- Port is the TCP port of the endpoint. By default,
1433is assumed.